Decrypting Google Chrome Passwords on macOS / OS X
There are a number of open source programs out there that decrypt passwords that you store in Google Chrome. However, all of these implementations are for the Windows OS only. What are we macOS users to do when we need a way to quickly dump all of our stored passwords in Google Chrome?
The current way of exporting passwords from Google Chrome is to open the Chrome browser, navigate to settings, then click “manage passwords”, then be presented with the following for each of your passwords that you want to access.

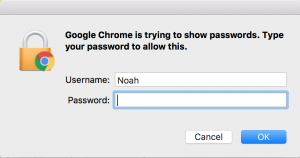
Who needs it! This is very inconvenient, and it mandates that you know the password of the local user on whatever box you’re on.
We can get around this by directly querying the Google Chrome SQL database that is stored in “~/Library/Application Support/Google/Chrome/Profile */Login Data” on macOS.
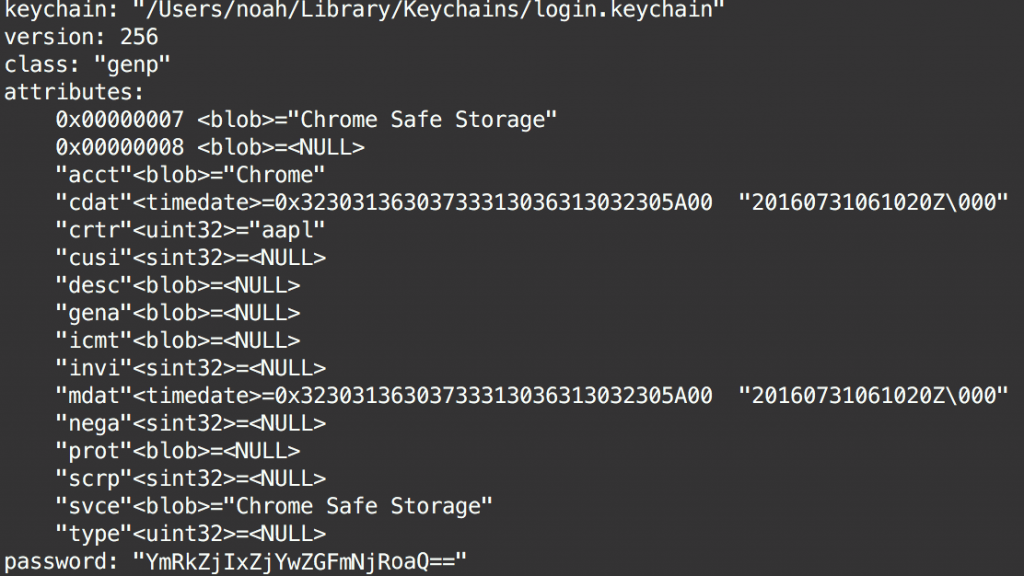
For each password that you have saved in Google Chrome, there is a field that looks something like this in this “Login Data” database:
 For this user we have this encrypted blob of data that begins with v10. What kind of encryption you ask? Well, lets refer to the Google Chromium Source Code for that information. In this source code we find the following information:
For this user we have this encrypted blob of data that begins with v10. What kind of encryption you ask? Well, lets refer to the Google Chromium Source Code for that information. In this source code we find the following information:
Encryption Scheme: AES-128 CBC with a constant salt and constant iterations. The decryption key is a PBKDF2 key generated with the following:
- Salt: The salt is ‘saltysalt’ (constant)
- Iterations: 1003 (constant) for symmetric key derivation.
- IV: 16 spaces.
- Hashing function: sha1
- Password: This is the important non-constant part. What we need is stored in the user’s keychain as “Chrome Safe Storage”. What is beautiful about this, is that we do not actually need the user’s keychain password to access this Safe Storage Key. We can directly call the macOS security process, through the command line using ‘security find-generic-password -ga Chrome’, to present the following dialog:
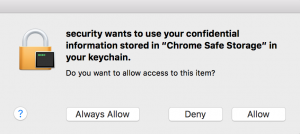
Booyah, we got the Chrome Safe Storage key without having to confirm the user’s password! (Note, not actually my password)
So the AES decryption key is generated through PBKDF2(‘sha1’, safeStorageKey, ‘saltysalt’, 1003). Okay so all of this information is great, but how can we use this to make an automated process that goes through our database, and decrypts each entry. Let’s use Python, because Python is the best. Better yet, lets use Python with zero dependencies, so that we can run this script on any macOS system, and have everything done in less than 5 seconds! Typically, AES decryption in Python is done through the wonderful cryptography library but alas, it is not a native library. We can leverage the OpenSSL command line tool, and use some clever pipe and redirects to send in a base64 copy of our encrypted password, and a hex copy of our PBKDF2 decryption key.
I have implemented the above in the following repository on my Github. It spits out something like this:

Interesting Note: What is so peculiar about this, is that Google does not protect it’s keychain entry! You can halt 99% of malicious use cases if the user has to verify their password in the security process instead of just clicking “accept” on the dialog. Google can fix this by just making the entry “Ask for Keychain password” when we try to access it outside of Google Chrome… Right? Actually, no, they cannot.
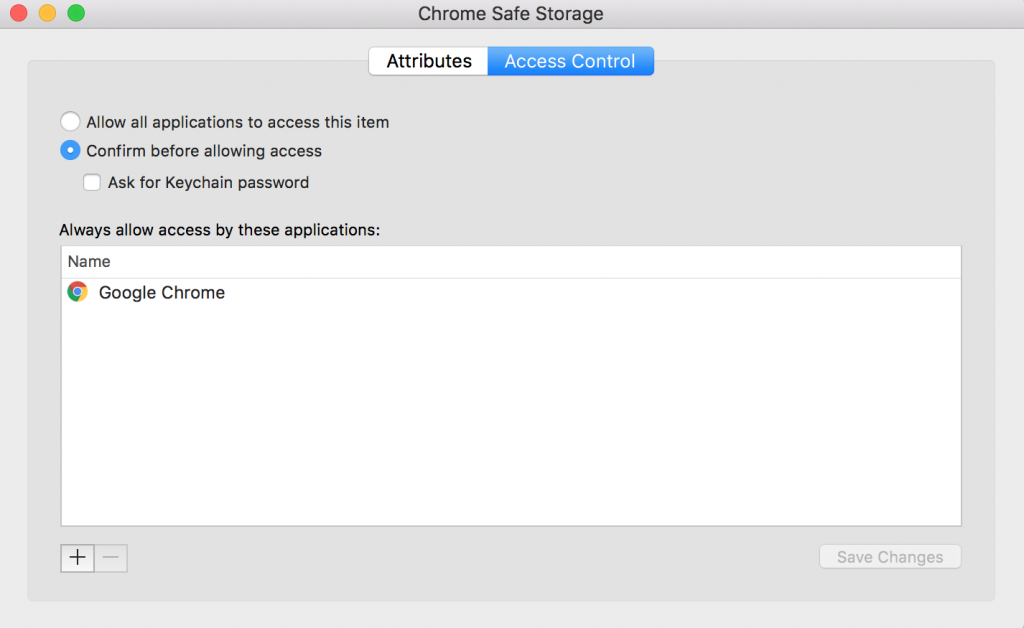
If Google wanted to make this be the case, then they would need to modify their call to the security process, when they initially create the Safe Storage Key, to require that the user verify their login information if they want access to the information. If we look at the “security add-generic-password” manual, we see that there is not an option to do this programmatically. Apple should seriously consider offering this feature to developers, so that they can better the digital safety of their users.
Also note: It is very trivial to write a few lines of shell / python that will essentially force the user to click “Accept”, by repeatedly blasting them with the prompt until allow access. Checkout the Github link for the program to see that in action.
TLDR; You can use this program, to decrypt / extract Google Chrome passwords on macOS / OS X. It is the only program for macOS / OS X that does this, and is 100% native to macOS / OS X, no dependencies are necessary. You can (for fun) add a few lines of code to have this extract the passwords, upload them to a remote FTP server, and then remove any trace of the program from the computer. Great for forensics, great for dumping all your passwords in one fell swoop.